Isolation
Introduction
Discover the core principles and benefits that drive the development of OBLV Deploy
What is OBLV Deploy?
OBLV Deploy provides a solution to ensure data security throughout the processing stages by using secure enclaves. Data Protection regulations are a key concern of every organisation in every country. While at-rest and in-transit data protection solutions are widespread, the security of data during processing doesn't have a well-established and approachable solution. OBLV Deploy fills this gap using enclaves to provide:
Attestation
OBLV Deploy is a confidential computing solution. If you are new to the field, see the Confidential Computing page, where the topic is covered from the basics.
OBLV Deploy Unique Features
OBLV Deploy and standard enclaves like AWS Nitro Enclaves offer robust security features providing isolated runtime and attestation documents to verify the integrity of the environment. However, OBLV Deploy provides additional features to enhance security, usability, and performance.
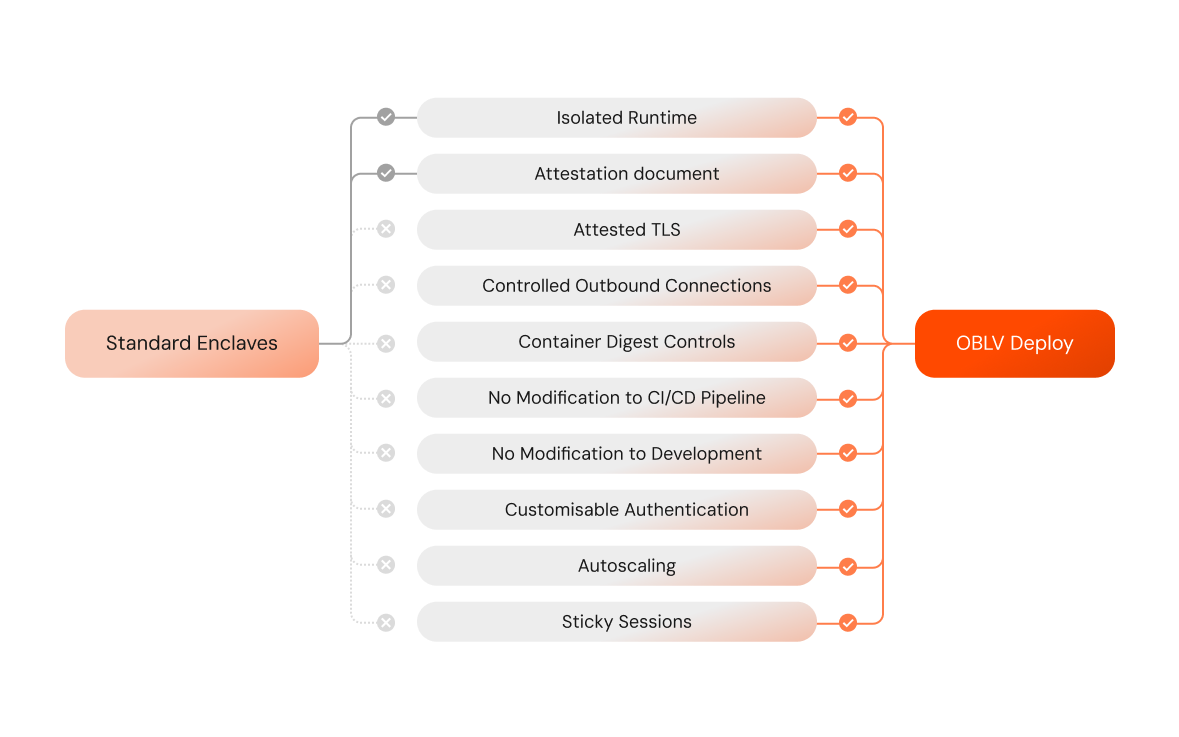
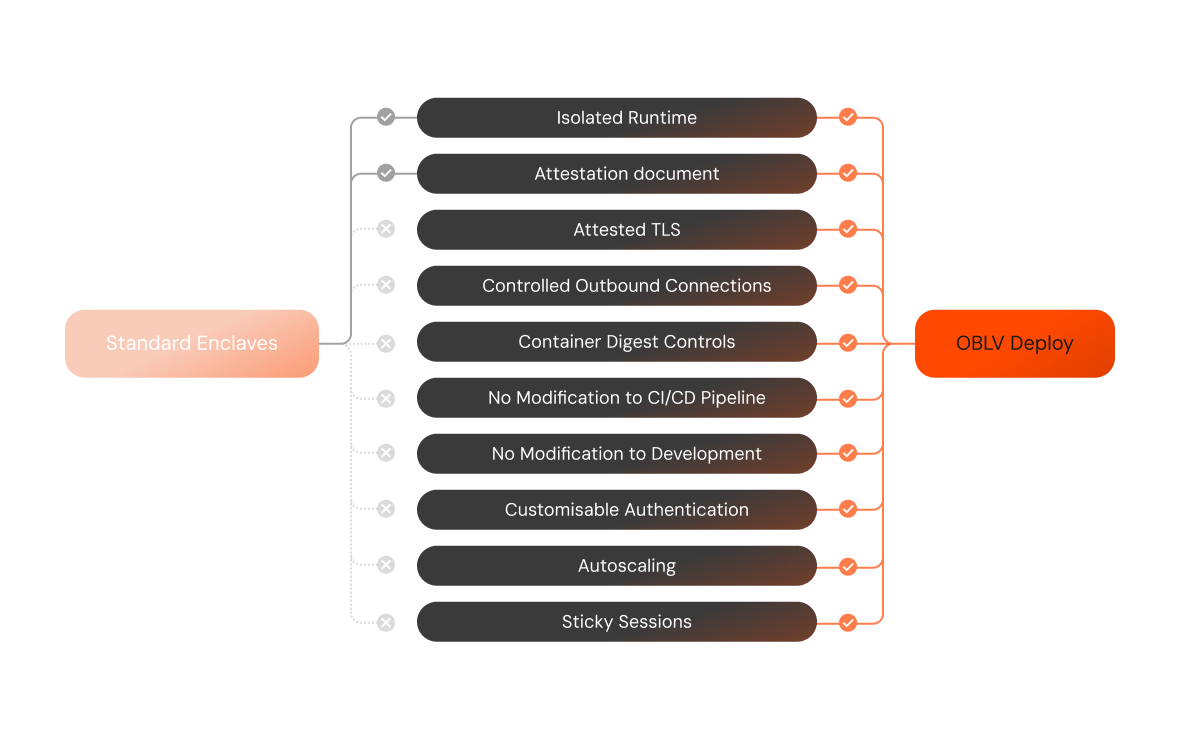
Security and Flexibility
OBLV Deploy extends the basic feature set of standard enclaves with attested TLS, ensuring that all traffic entering and leaving the enclave is encrypted and verified against a trusted certificate. Moreover, OBLV Deploy supports outbound connection controls, which allow precise control over network traffic, ensuring that only authorised connections are made. Container digest controls provide another layer of security by ensuring that only containers with verified digests are executed.
Simplified Operations
OBLV Deploy seamlessly integrates into existing workflows. It requires no modification to CI/CD processes or development environments, making it incredibly straightforward to adopt without disrupting current operations. OBLV Deploy can be deployed to any AWS region.
Customisation and Performance
OBLV Deploy extends the basic feature set of standard enclaves with attested TLS, ensuring that all traffic entering and leaving the enclave is encrypted and verified against a trusted certificate. Moreover, OBLV Deploy supports outbound connection controls, which allow precise control over network traffic, ensuring that only authorised connections are made. Container digest controls provide another layer of security by ensuring that only containers with verified digests are executed.
What's Next?
Now that you know the solution OBLV Deploy provides, you can start learning how to use it. In this documentation, you'll find two ways to use the getting started page. If you're an administrator, the OBLV Deploy team recommends you start with the Quick Start Guide. However, if you're an end-user, see the Making an Attested Connection page.